Ho Ho Ho! It’s time for the holidays around these parts but things aren’t quite as silent as one might hope. Thanks to a big holiday present from the International Telecom Union (ITU) the whole world is watching as operators drink eggnog and debate the free world as we know it. With this in mind, we’re tackling one of the biggest topics in networking today: DPI.
It seems that the whole world is in an uproar about Deep Packet Inspection (DPI). As many of our readers may know, DPI is about inspecting internet traffic as it transverses large networks (ISPs, DataCenters, Enterprises, etc.). In the case of this ITU ruling, we’re talking mostly about ISPs, and the big ones at that. It’s important to understand that DPI isn’t some big scary monster, in fact, if you’re using an SBC or a content-aware firewall, you’re already using DPI in your business today. Why then is it so scary?
What is DPI?
So before we go any further, let’s quickly talk about what Deep Packet Inspections (DPI from here on out) is. To understand DPI we have to understand how Switches and Routers work.
Switches and Routers connect computers together by exchanging packets of information between them. Simply put, switches and routers decide where information needs to go and how it should get there. You can think of switches like small intersections within a city. The roads are wires or lanes to your computer, with the intersection being the point where the traffic criss-crosses and gets directed on it’s way. Routers are more like large highway access ramps or interchanges. They often have rules about who can get on or off via that interchange (no trucks! one-way! keep left!) and how.
 In today’s world, most routers and switches tasked with managing the flow of traffic do so with as little intelligence as possible. They look at where the driver wants to go and, as fast as possible and with as little effort as possible, sends them blindly on their way to the next point in their journey, which, depending on your application, may or may not be what you want. Then there’s DPI.
In today’s world, most routers and switches tasked with managing the flow of traffic do so with as little intelligence as possible. They look at where the driver wants to go and, as fast as possible and with as little effort as possible, sends them blindly on their way to the next point in their journey, which, depending on your application, may or may not be what you want. Then there’s DPI.
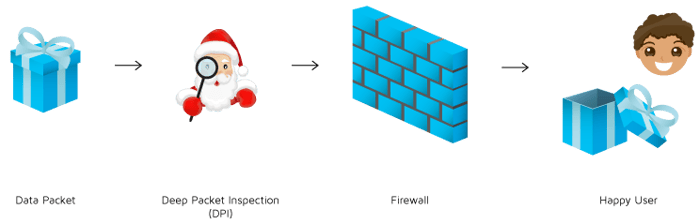
DPI is like an inspection of the traffic and analysis of it, before it goes on it’s way. Using the same analogies as above, DPI might be like a policeman at a freeway on-ramp inspecting every cargo load that was being taken onto the highway. There might be various reasons for this inspection – weight restrictions, terrorist threats, lost children, etc. This is a “deeper inspection” into your car, just like DPI is a deeper inspection into your computer’s data packets.
How Does DPI Work?
DPI is generally performed one of two ways: either by the Firewall which sits between the router and your switch or using a fiber tap to send the network traffic elsewhere for analysis. Today w’re focusing on Firewalls as the case for batched processing is much more murky. DPI enabled firewalls differ from Switches and Routers. Whereas switches are mainly concerned with frames (layer 2 OSI) and Routers are concerned with packets (layer 3 OSI), DPI-enabled Firewalls examine packets from frame to actual application structure (layers 2-7). The key difference here is that frames and packets have a set of directions which are supposed to be explicitly followed by the routing system. With the introduction of application sensitive filtering routing can be done not just on the basis of where the packets and frames want to be sent, but on the basis of where the administrator wants a given application sent. DPI represents one of the first times in history that packets can be diverted based not on a users commands but on the basis of a firewall segregating traffic. This sounds really bad. Why would anyone want this?
The Datacenter of Tomorrow
You sign up for access to the Datacenter of Tomorrow. You’re provisioned inside of the DC, you’re administrating your servers but you’re getting a sluggish response on your voice application. With the click of a mouse you’ve designated your firewall to pickup your voice traffic and prioritize it above other traffic you’re sending out. Now your voice is working great, but what about the rest of the DC? It turns out that the operator is able to control which applications get prioritization, not with packet tagging, but simply by entering the name of the app into their console and promoting it in a priority list. Let’s say one particular application is giving you trouble. Previously you’d isolate the packets and try to figure out what the heck was sending out so much trash on your network. Now, you grab the application ID from your console and those packets never make it past any of your firewalls. But what about today?
Toto, I don’t think we’re in Kansas Anymore
There is a sincere and real risk that content aware firewalls will damage the ability of individuals to communicate openly on the Internet. Repressive regimes, particularly in the middle east, use technologies like Blue Coat content filters to block “bad” traffic, identify dissidents and provide evidence in State-Sponsored inquisitions. These are not good side-effects of DPI, and for many parties these aren’t side-effects at all, but rather goals. This is the scary side of DPI, the idea that your ISP can know not just that you’re sending packets, but what those packets contain. This is the crux of why everyone is so up in arms, but how do we ensure that technology advances while still retaining personal freedom? We think of this from both a societal and economic perspective, and with the latter being easier to explain we’ll discuss this idea from that perspective. We believe that personal freedom and privacy are tremendously important but we’re focusing on the economics today.
The Datacenter of Today
2600hz is obsessed with VoIP, and one of the biggest issues in VoIP is fraud. There are so many different ways to defraud companies in VoIP, but one of the ones we see most often is attempting to steal credentials and create fraudulent calls. We leverage Kamailio as our Session Border Controller which leverages DPI to confirm packet intent against a set of heuristics. This dramatically reduces fraud on our network and would be impossible if we only used layers 2-3 for analysis. Because our border equipment supports analysis of packet intent, we can match the packet up against a registry (username/password) to authenticate them. Referencing a database inside of a firewall and applying a policy is hardly new, but doing it based upon the application signature instead of the header is a relatively recent innovation.
The Bottom Line
We at 2600hz believe that DPI is necessary for the evolution of the Web. As Spiderman’s Father once said “with great power comes great responsibility”. DPI has the power to make life a living hell for dissidents, but it also is key to moving massive networks forward. Understanding DPI is going to become an important portion of network engineering, but it has the potential to make many of the services we use today function in a better and more congruous manner. DPI is here to stay, and frankly it’s been here for a while.
