BYOD Versus CYOD: User Choice in a Policy Driven World
Humans crave freedom, but is freedom of choice practical in the Enterprise World? Since the iPhone launched in 2007, there’s been a remarkable trend. Experts have dubbed it: ‘Bring Your Own Device’ (BYOD). Today we’re discussing a new phenomenon which we call 'Choose Your Own Device’ (CYOD).
BYOD came about because users wanted freedom: the freedom to utilize services without company prescribed kitsch. However, IT teams make it difficult for users to acquire the necessary resources. This results in users acquiring resources outside the corporate FireWall. Enterprise Security groups are not friendly to uncertified equipment (see for yourself by plugging into Google’s Production LAN with an unknown Ethernet Device). The problem for these Security teams is simple: users engage in 'Shadow IT’. Dropbox, Box, and BYOD entered Enterprise this way, then spread like a wildfire. CYOD is an attempt by the Security guys to allow users some freedom while still retaining control over their Mobile Workforce.
Let’s differentiate the two approaches.
Bring Your Own Device (BYOD)
In a BYOD environment users connect to the network via their chosen equipment. Policies are usually enforced at the server level and device-level control simply isn’t possible. Additionally, since management capabilities are restricted to user policies, the way users consume information is frenzied. Can you imagine supporting an Android based workforce of 2000 users BYOD'ing in excess of 100 different builds? On top of all this, BYOD policies are not sensitive to user location: it doesn’t care whether users are on the road or in the office! This makes the work of security unnecessarily difficult, which puts a strain on corporate security resources. Now, lets look at the environment CYOD has to offer.
Choose Your Own Device (CYOD)
In the CYOD world, users are given a choice between several, purposefully selected Operating Systems. Depending on the environment, iOS and Android are offered with a wide variety of third OS choices (Blackberry, Windows, or maybe WebOS). If users have a device that fits into one of these categories, they are welcome to connect it. The reason for this is a set of technologies the industry refers to as Mobile Device Management (MDM). MDM applications allow finer control than simple mail filters, contain Remote Wipe functionality, and they even allow VPN provisioning and access policy control. MDM systems are usually context-aware and perform geo-fencing to isolate user information access. Geo-fencing is a useful function which blocks access to sensitive information outside specified zones. While these feature sets are difficult to employ across an endless spectrum of devices, they’re easy to implement on a large but controlled group of devices.
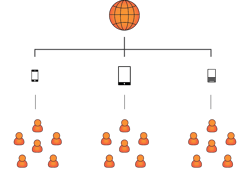
Even if MDM applications support Android and iOS handsets, I doubt many will complain: CYOD is about Enterprise Security Groups returning to reason.
2600hz and CYOD
At 2600hz we are excited about CYOD. We see the end-user’s choice in device as complimentary to our approach of supporting all types of standards based devices. Perhaps more importantly, CYOD plays directly into our support of users’ controlling their own communication devices. While video chat and good camera quality may be essential for one user, background apps and tethering may be essential to another. 2600hz says: let user preferences drive real decisions–not the corporate IT department.
